MySQL procedures can introduce security risks if they are not designed and implemented properly. Here are some best practices for ensuring the security of your MySQL procedures:
1. Limit access to procedures: Only grant procedure execution privileges to authorized users or roles. You can do this by setting appropriate privileges for the `EXECUTE` permission in the `GRANT` statement.
2. Use parameterized queries: Use parameterized queries in your procedures to prevent SQL injection attacks. Parameterized queries use placeholders for user input, which are replaced with sanitized values during query execution.
3. Sanitize user input: Always sanitize user input to prevent malicious input that can compromise your database security. Use input validation techniques to ensure that user input adheres to the expected format and data types.
4. Avoid using dynamic SQL: Avoid using dynamic SQL in your procedures, as it can introduce SQL injection vulnerabilities. Instead, use static SQL statements that are validated during compilation.
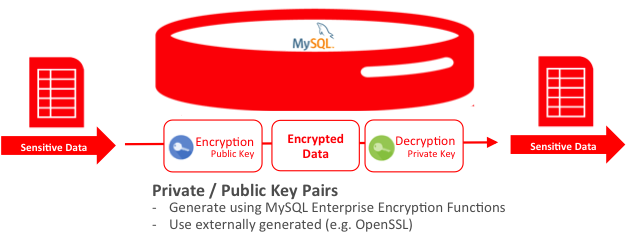
5. Encrypt sensitive data: If you store sensitive data in your procedures, encrypt it using MySQL's built-in encryption functions or third-party encryption libraries.
6. Use secure connections: Use SSL/TLS connections to encrypt data in transit between your MySQL client and server. This helps prevent eavesdropping and data interception.
7. Audit procedure activity: Enable MySQL's audit plugin to log procedure execution activity. This can help you identify any security threats and track who is accessing your database procedures.
8. Keep procedures updated: Keep your procedures updated and patched with the latest security updates to address any known security vulnerabilities.
9. Use role-based access control: Use role-based access control (RBAC) to control access to procedures based on user roles and responsibilities. RBAC allows you to assign permissions to specific roles and then assign those roles to users, rather than granting permissions directly to users.
10. Monitor procedure activity: Monitor procedure activity using MySQL's general query log or slow query log to detect any unusual behavior or activity that may indicate a security threat.
11. Use stored procedures instead of direct SQL: Use stored procedures instead of direct SQL queries to protect against SQL injection attacks. Stored procedures are pre-compiled and validated before execution, making them more secure than ad hoc SQL queries.
12. Secure the server environment: Secure the server environment where your MySQL database is running by using strong passwords, firewall rules, and other security measures to prevent unauthorized access and protect against security threats.
By following these best practices, you can help ensure the security of your MySQL procedures and protect your database from security threats. It is important to stay vigilant and proactive in your approach to database security, and to stay informed about the latest security threats and best practices for preventing them.




.png)